
by Dave Silver
Identity management is at the forefront of efforts to implement zero trust (ZT) across the federal government. Under ZT, no identity, device, network, application, or data is deemed trustworthy. This shift in thinking puts the onus on government agencies to assure that only “the right person with the right privileges can access the right information at the right time.” It also elevates the requirements for access authorization models, asserting they must incorporate enterprise-managed identities and employ phishing-resistant multifactor authentication (MFA).
Available solutions include Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). Simply put, RBAC associates access permissions with a user’s role within an agency or organization. The National Institute of Standards and Technology (NIST) expounds on this definition, adding “Role permissions may be inherited through a role hierarchy and typically reflect the permissions needed to perform defined functions within an organization. A given role may apply to a single individual or to several individuals.”
ABAC, per NIST, is “an access control method where subject requests to perform operations on objects are granted or denied based on assigned attributes of the subject, assigned attributes of the object, environment conditions, and a set of digital policies that are specified in terms of those attributes and conditions.”
ABAC can be a more stringent and reliable form of access control because it relies on real-time decision making using attributes obtained at the same time. Coupled with its capacity to verify entity identity, ABAC is seen as foundational to both identity management and ZT. It also is important to note that ABAC supports RBAC since roles, like any other subject characteristic, are handled as attributes.
ABAC can be a more stringent and reliable form of access control because it relies on real-time decision making.
ABAC: A Closer Look
ABAC protects objects from unauthorized access by subjects and prevents non-permissible operations from being performed. It operates based on a complex Boolean rule set that evaluates a variety of attributes in combination to make authorization decisions. Notably, these attributes, expressed in policies, can be assigned to the subject, the object, the environment, or the action to be performed.
Subject attributes can be as simple as clearance (e.g., top secret) or name of the organization currently assigned to (e.g., accounting department). Notably, the subject can either be a human entity or a non-person entity. The object may have attributes such as object type, classification, or author/owner. The data owner uses data tagging to assign attributes to object data as needed to enhance the granularity, and therefore robustness, of access control decisions.
Environmental conditions (represented as attributes) are dynamic properties independent of the subject and object such as geographic location, date, time, or time zone from which the access request originates. Finally, action attributes include read, write, edit, delete, or view.
In its simplest form ABAC makes authorization decisions based on evaluating the conditional logic specified in the applicable digital access control policy. As shown below, the basic ABAC model possesses:
- A Policy Administration Point (PAP) user interface to create, test, approve, manage, and store digital access control policies.
- A Policy Decision Point (PDP) to render an access control decision based on applicable policy.
- A Policy Information Point (PIP) to retrieve remaining attributes (or other data) as required by the applicable digital policy.
- A Policy Enforcement Point (PEP) to enforce the PDP’s decision.
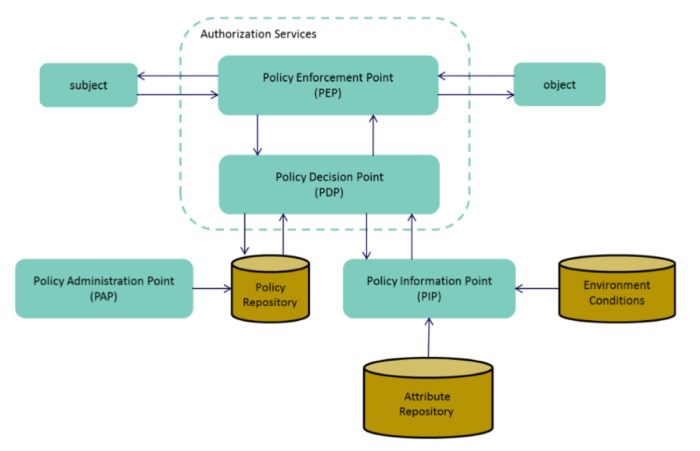
Basic ABAC Components (Source: NIST SP 800-162)
Not shown but underlying the architecture is a Context Handler or workflow coordinator that facilitates interaction between various components.
ABAC is typically implemented using eXtensible Access Control Markup Language (XACML). XACML provides a flexible common language for expressing and sharing fine-grained access control policies.
Benefits of ABAC
ABAC comes with many benefits and only one notable drawback: the mapping effort associated with developing authorization policies/metapolicies is substantial. The benefits include:
- Real-time authorizations
- Scalability in terms of both subjects and objects
- Flexibility
- Ability to craft policies that range from simple to complex
ABAC comes with many benefits and only one notable drawback.
Notably, major cloud providers, including Amazon Web Services and Microsoft Azure, offer ABAC solutions.
• • •
As access authorization requirements become more stringent in response to the growing sophistication and persistence of cybersecurity threats, solutions such as ABAC will become more commonplace. Its scalability and flexibility, coupled with its dynamic nature, offer next-level protection against improper access authorization.