Explore our other capabilities:
Identity, Credential & Access Management | Enterprise IT Modernization & Optimization | Software Solutions Development & Sustainment

Cybersecurity Compliance & Operations
Cyberthreats to federal systems and networks are real and pervasive. To manage risk and demonstrate due diligence, federal agencies must comply with growing numbers of statutes and regulations. Interpreting this guidance and developing responsive solutions can present major challenges.
Electrosoft employees are well-recognized subject-matter experts in the cybersecurity domain. We possess over 20 years of front-line experience building secure federal systems and defending them against internal and external threats. Over this same period, we have (co)authored numerous cybersecurity standards and other technical publications for the National Institute of Standards and Technology (NIST), giving us rare insights into the requirements they impose. Our thought leadership efforts do not end there. We advance the cyber-security field through knowledge sharing in forums such as conferences, technical publications and blogs.
Now is an especially pivotal time for federal agencies. The government is concurrently modernizing its systems and moving to a zero-trust architecture (ZTA). ZTA requires a multi-pronged, holistic approach incorporating an effective risk management strategy for user and device authentication and access provisioning. Network perimeter approaches will no longer suffice. Users and networks will not be trusted by default. Outdated systems and the data they contain will need to be updated, replaced or transitioned. It is at once an exciting and challenging shift that will enhance agencies’ resilience against cyberattacks and insider threat.
Electrosoft’s cybersecurity proficiencies encompass six distinct areas of specialization. Whether architecting and/or developing secure systems, obtaining and maintaining security authorization or operating Security Operations Centers (SOCs) on behalf of federal agencies, we are uniquely qualified to help. We know the latest methodologies and technologies. We understand federal mandates and can help customers interpret them.
We tailor our efforts to the specific needs of each customer and offer wide-ranging services. We develop and manage risk-effective and compliant security programs. We conduct assessments, analyses and testing. We obtain and maintain Federal Information Security Modernization Act (FISMA) and Federal Risk and Authorization Management Program (FedRAMP) compliance. We architect and implement ZTA. We operate SOCs and much more.
When you need cybersecurity services and solutions, think Electrosoft.
Areas of Specialization

- Security & Privacy Policy & Architecture Read More >

- Security Assessment & Authorization; Ongoing Authorization Read More >

- Vulnerability Management, Analysis & Penetration Testing Read More >

- Cloud Security Services; FedRAMP Compliance Read More >

- Security Operations Center & Managed Detection & Response Read More >

- Security Engineering; Zero Trust Implementation Read More >
Client Stories
Cybersecurity Data Visualization – Driving Innovation and Excellence in Cybersecurity Readiness
-

- A unified combatant command within the Department of Defense (DoD) provides global air, land, and sea mobility to move troops, equipment, and supplies for military operations in times of peace and wa... Read More >
Ongoing Efforts to Secure a Defense Supply Chain Continue to Yield Impressive Results
-

- A defense agency providing command and control for transporting, distributing, and sustaining personnel and assets worldwide relies on information technology to achieve its Read More >
Implementing Multifactor Authentication in a Standalone Operating Environment
-

- A small independent federal agency chartered with responsibility for select commerce activities sought to comply with Executive Order (EO) 14028, which requires agencies to implement specific actions... Read More >
Improving Cybersecurity Through Better Tools, Processes and Automation!
-

- One U.S. civilian government agency recognized that it was a high-priority target for cyber threats and attacks and that its cybersecurity program could be improved. Read More >
Transforming a Defense Agency’s Approach to IT Operations Compliance and Audits
-

- When one defense IT operations organization resolved to become proactive when managing and monitoring compliance and risk mitigation, Electrosoft implemented Read More >
Supporting Digital Transformation with Cloud Migration
-

- Electrosoft supported the successful migration of multiple legacy web applications to the cloud environment for a defense agency, ensuring Read More >
Improving Enterprise Security through User Access Governance
-

- Electrosoft provides Identity, Credential and Access Management (ICAM) expertise to enhance the cybersecurity posture of a civilian agency that oversees many U.S. financial institutions. Read More >
Making Security Documentation more usable to Cybersecurity Practitioners through Informative References
-

- Electrosoft assisted the National Institute of Standards and Technology (NIST) to develop and implement the National Cybersecurity Online Informative References (OLIR) Program to provide a standardiz... Read More >
Securing an Evolving Cyber Environment through Effective Patch Management
-

- Electrosoft is executing a patch management solution for a Department of Defense (DoD) agency that maintains enterprise software for 55,000 endpoints. Read More >
Protecting U.S. Economic Interests through Cybersecurity and Privacy Services
-

- Electrosoft’s experienced team of Cybersecurity and Information Privacy professionals supports the security and privacy efforts of a civilian agency that promotes and protects U.S. economic interes... Read More >
Developing Cybersecurity, Identity Management, and Encryption Standards and Guidelines
-
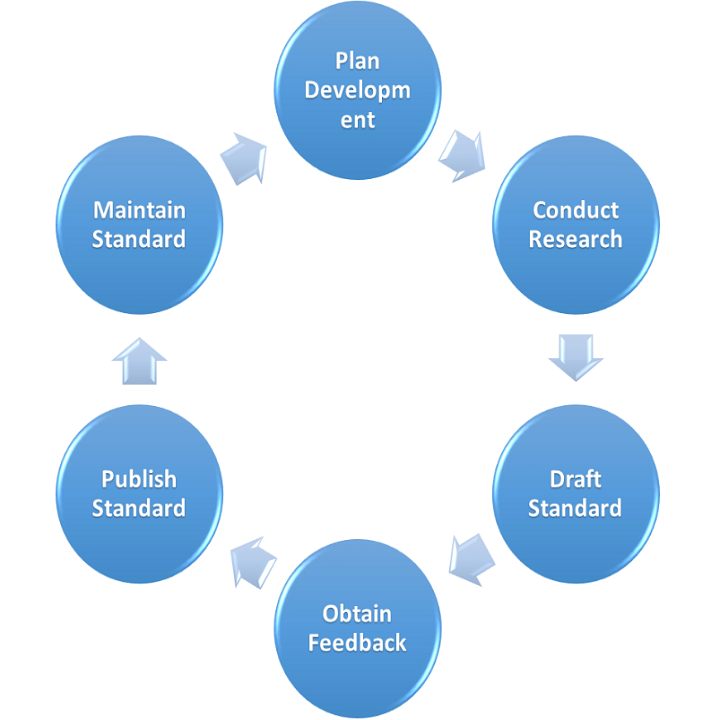
- Electrosoft’s team of world-class experts worked closely with Government researchers to define, develop and refine needed technical standards and guidelines. Read More >
Providing Operational Support for HSPD-12 Program Management Office
-

- Electrosoft experts analyzed emerging policies, standards and trends related to Federal identity, credential and access management to support a Civilian Department’s desire to remain at the leading... Read More >
Providing Security Analyst Services for Emerging Health Technology
-

- Electrosoft performed in-depth research to identify, analyze and validate emerging technologies, healthcare trends, policies, standards and guidelines. Read More >
Improving Operational Efficiency with ERP-Enabled and FIAR Compliant Business Solutions
-

- Electrosoft successfully planned, reengineered and implemented next-generation business processes by leveraging the U.S. Navy's investment in an enterprise resource planning (ERP) solution, which inc... Read More >
Overseeing New Technology Incubation to Enhance the Defense Supply Chain
-

- Managing the global defense supply chain is a challenging task that relies on information technology (IT) for mission accomplishment. One defense support Read More >
Improving Visibility and Performance of Critical Cybersecurity Program Through Automated Reporting
-

- Electrosoft created a set of individualized daily reports for each PoC and used the Report Builder subscription service to email reports to each PoC. In this way, PoCs had a daily snapshot of overall... Read More >







